
OR
Dark web is the underworld of cyberspace
Published On: June 7, 2020 11:20 AM NPT By: Krishna P Bhandari
In January 2020, several European news outlets, including The Daily Telegraph, reported that a famous set of antique jewellery were offered for ransom on the dark web. The diamond studded pieces worth almost a billion dollars were looted from a museum in Dresden in 2019. It was reported that Israeli investigators were offered a few of the pieces as a ransom. The messages on the dark web also claimed that it would be futile to try to identify and locate them. The ransom was also to be paid off in Bitcoin, a digital currency.
Imagine a standard business scenario. A business based on sales of a product or service needs a market, a set of products, a marketing campaign. Add to that the corollary mechanisms of customer support, complaints handling and the mechanism becomes a full-fledged commerce. Products, prices, market forces, supply, demand, buyers, sellers and so on.
The dark trade
If a product is not a legal product but still sought after by people in the market, buying would also be as illegal as selling. So neither the seller nor the buyer want to be visible to the outside world. They want to be anonymous, at least to produce, sell, buy and consume illicit products. Suddenly the whole market ecosystem for such products goes underground or anonymous. No mass marketing, no billboards, no well-known addresses, no public phone numbers. Still the market continues to operate and business thrives. While ensuring anonymity and hiding the activity, the buyers continue buying, sellers continue selling, dodging the authorities and thriving in darkness. The normal society cannot see. It is ‘dark’ from their perspective.
The dark network
The Internet also functions like a normal social mechanism. Activities happen. Correspondences take place. Business and commerce is carried out. People can search things. People can publish things that can be searched by others. That is the normal, visible Internet. Like the hidden world of illegal trade, there is also a hidden Internet, though not fully illegitimate. On the illegitimate side, people access, buy and sell drugs, weapons, child pornography and many other illegal stuff using the platform of this hidden Internet. People with radical and extreme agenda use it to recruit cadets and lure victims.
As it is not seen by the normal populace, it is aptly called the dark net, the dark web etc. The dark net uses all the technologies of the normal Internet combined with specific practices, tools and technologies to make the content and transactions not visible to the normal audience. Like the illegal physical market, the people transacting on the dark web need to be specifically aware of the products, services and the places to conduct transactions. You have to belong to the underworld to access it. Or you have to be drawn into it, by those already inside it.
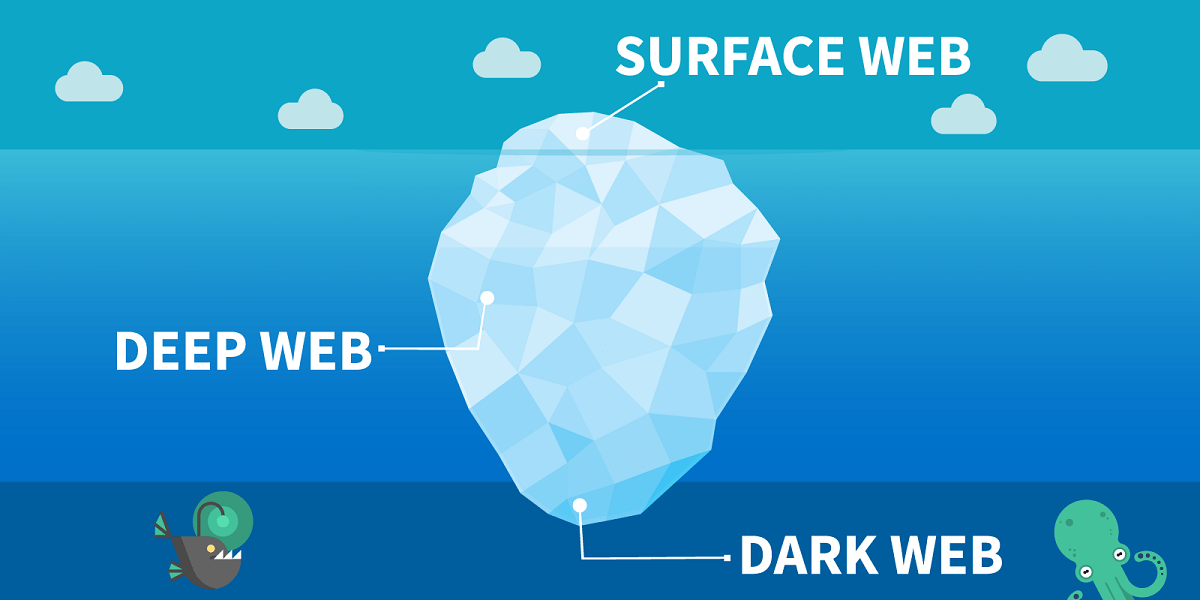
However, the dark net that is used for illegal activity and trade is only a small fraction of the so-called deep web which is much larger than the visible Internet. Only a small portion of the activities performed in this hidden network is illegal.
How to access it?
As is obvious, the dark net is not accessible through standard means. The sites cannot be browsed with normal, day-to-day Internet browsers. Specially designed browser software is needed to access the darknet. On top of that, the user needs to specifically know what he or she is accessing. In the normal scheme of things, Internet surfing usually starts with a search engine. Just type in the things you want to search into the search box and the rest is done by the engine. You are guided to the site containing information about the searched topic. But the dark net is different. Its contents cannot be searched using standard search engines. Search engines cannot crawl and index their contents. Special tools such as the TOR (The Onion Router) browser are used to browse the darknet. These browsers are designed to anonymize the Internet surfer and make access possible to the underworld of the Internet.
The TOR project has the word ‘Onion’ in it to reflect the many layers that it has to traverse to achieve anonymity. The client computer using the TOR browser thus cannot access the information source directly. It goes through a multiple layer of servers or devices before reaching the actual source of data. This multilayer abstraction is intended to ensure the anonymity of the user so that neither the content source nor the user can be traced using standard Internet tools.
Why is it dark?
The normal or clear net is made visible to the world by various technologies. The foremost is the ability of search engines such as Google to search and index the web pages. Another technology powering the clear net is the domain name system or the DNS. It translates the common internet addresses such as abc.com to the actual address used by computers, aka the IP address. However, most of the dark net sites are visible only through IP addresses. So they cannot be accessed through common domain names. That makes it so much more difficult to remember, manage and keep track of these addresses. Since the access modality and the general structure is not visible through usual means, it is referred to as dark. Its name ‘dark’ is further accentuated by the illegal and dark activities performed with the help of the platform.
Once you get the means and the knowhow to enter the dark net though, it might be as luminous as any other Internet content. If one gets exposure inadvertently or is drawn into it, the dark net may truly have a very dark side indeed.
Why is it used for crime?
The first aim of a criminal is not to get caught. For that, they want as little of the trail of their activity to be maintained as possible. Since the dark net has some provisions to help enhance anonymity, criminals love it. Because of the increased difficulty to trace an event back to the person, the illegal activities are hard to track and control. That is perhaps the main driver of high use of dark net for criminal activity and for spreading illegal material. Commercial transactions dealing in arms, drugs, child pornography or weapons can be easily performed with reduced risk of prosecution. Moreover, the financial transactions are performed using digital currency or shady bank accounts which are difficult to locate and trace back to a person.
Apart from trade, activities such as propaganda spreading, recruiting radicals for extremism etc. are also performed using network platforms provided by the dark web. German data security firm GDATA lists some of the things traded on the darknet. They include items ranging from forged credit card numbers to arms and ammunition, contract killers to counterfeit IDs and university degrees, computer viruses and malware to deadly poison, marijuana to even Uranium. The actual gamut of items traded over the dark net would obviously be much wider and more sinister.
Is it only illegal?
No. The darknet was originally not intended for illegal activity. In the late 1990s, the encrypted and hidden communication channel was envisaged to protect the sensitive communication of spies. While full realization of the dream was not achieved, the concept soon bifurcated into a network of activists for human rights and political dissent.
Apart from the various distinct uses of its own, the dark web or the deep web also has a major role in keeping the normal Internet operational. Every legitimate website or network service has a hidden mechanism that need not and should to be exposed. These include the mechanism to manage the content, network and infrastructure of the normal network. Such privileged and internal activities are restricted to the hidden network. This same hidden network and related technologies evolved into the dark web. In terms of the resources, content volume and physical infrastructure, the hidden network is much larger than the visible network.
Moreover, the darknet is also useful for perfectly logical and positive activities. For example, an investigative journalist might want to use the dark web to covertly plan her research and sting operations. The platform can also be used for citizen activism against an authoritarian regime. This group of users, though having legitimate intentions, usually resort to the dark net to ensure anonymity and escape persecution, censorship and threat from authorities or society.
Darknet or dark web or deep web is a network similar to the visible Internet. The differentiator is the visibility of the network resources and the anonymity of the involved parties. It is a legal and legitimate network infrastructure that enables the visible network to function properly. It also enables a lot of online activity that cannot be performed in the open Internet because of the need of secrecy, anonymity or even persecution and fear from others. This ability to ensure anonymity is also being used for illegal activities. Still its good uses and importance for overall cyberspace is far greater compared to the bad uses. The dark nature has some benefits that are being used for good causes as well. Dark web is both the bedrock of cyberspace with positive and critical use as well as an underworld of the Internet having negative uses.
You May Like This
Deterrence in cyberspace
The key to deterrence in the cyber era is to acknowledge that one size does not fit all ... Read More...

Securing Nepali cyberspace
Narayan Koirala is an Information Security Practitioner/Information Systems Auditor, Cofounder/ Director at Eminence Ways. In conversation with My City’s Nasana... Read More...

Securing cyberspace
Nepal has to develop a comprehensive national cyber security strategy if it i s serious about protecting itself from cyber threats Read More...





Just In
- DoFE requests relevant parties to provide essential facilities to foreign workers traveling abroad
- Foundation stone laid for building a school in Darchula with Indian financial assistance
- 151 projects to be showcased for FDI in Third Investment Summit
- Police disclose identity of seven individuals arrested with almost 2 kg gold and more than Rs 10 million in cash
- NIMSDAI Foundation collaborates with local govt for Lobuche Porter’s Accommodation Project
- Home Ministry directs recalling security personnel deployed for personal security against existing laws
- Fake Bhutanese refugee case: SC orders continued pre-trial detention for seven individuals including former DPM Rayamajhi
- ADB Vice-President Yang pays courtesy call on PM Dahal















Leave A Comment